TwoFactorAdminLogin
From LimeSurvey Manual
Introduction
2-Factor-Authentication (2FA) is a way to add additional security to your account. It is called "two-factor-authentication" because two verification methods are used to access your account. The first "factor" is your usual password that is standard for any account. The second "factor" is a verification code retrieved from a 2FA application either from your computer or mobile device. For more details about 2FA and its importance, please visit the following article.
The plugin supports both TOTP (Time-based One-Time Password) and Yubikey authentication methods.
When TOTP is enabled, a 6 digits code (default value) has to be introduced when you log in to your LimeSurvey instance. If Yubikey is configured, when logging in, the Yubikey will create the code.
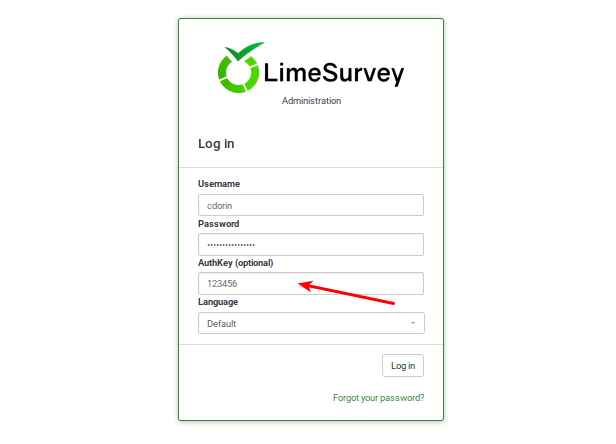
To learn more about this functionality, please continue reading below.
How to install the 2FA plugin
Since version 6.x the plugin is a core plugin. So just visit the Plugin Manager page and enable it from there (see below for more details).
Activate the 2FA plugin
To activate your 2FA plugin, access your LimeSurvey instance, and activate it from your Plugin Manager:
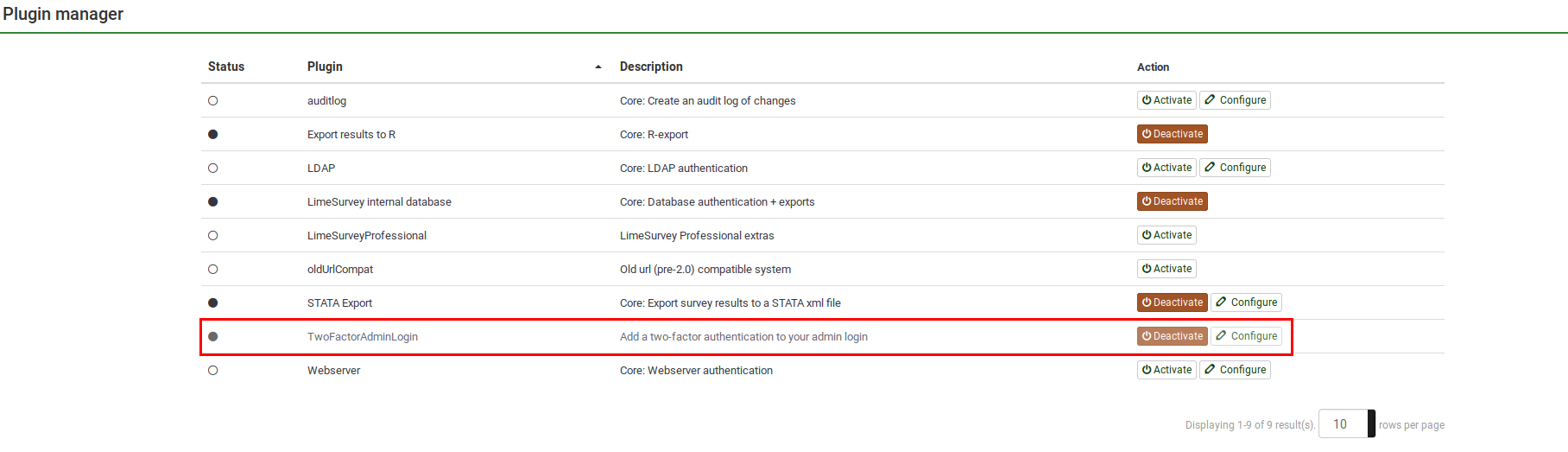
To check the default settings, please click on "Configure".
Plugin settings
The configuration page contains the following settings:
TOTP Settings:
- Issuer: The text typed in this box will be displayed in the app as issuer name.
- Digits: The number of digits the resulting codes will be. Please leave it at 6 for Google Authenticator.
- TimePeriod: The number of seconds a code will be valid. If you use Google Authenticator, please leave it to 30.
- Discrepancy: The amount of discrepancy is allowed for the client after the TimePeriod expires (seconds)
- Algorithm: The algorithm used to generate a hash:
- SHA1 (Default)
- SHA256
- MD5
Yubikey Settings:
- YubiCloud Client ID: Your YubiCloud Client ID for validating Yubikey authentication attempts. This is required to use Yubikey as an authentication method.
- YubiCloud Secret Key: Optional but recommended. When set, the YubiCloud responses' authenticity will be verified, providing an additional layer of security.
To obtain these credentials, you can sign up for a Yubico API key at the Yubico API key signup page.
General Settings:
- Force 2FA:
- Only prompt, no enforcement Users without 2FA token are redirected to 2FA creation after login
- Always enforce 2FA activation Users without 2FA token are redirected to 2FA creation after login, and no other action are available, except remote control.
Important: Don't forget to click on "Save" after updating your 2FA configuration.
2-Factor-Settings
Once you activated the plugin, a new menu item will be displayed on the top bar:
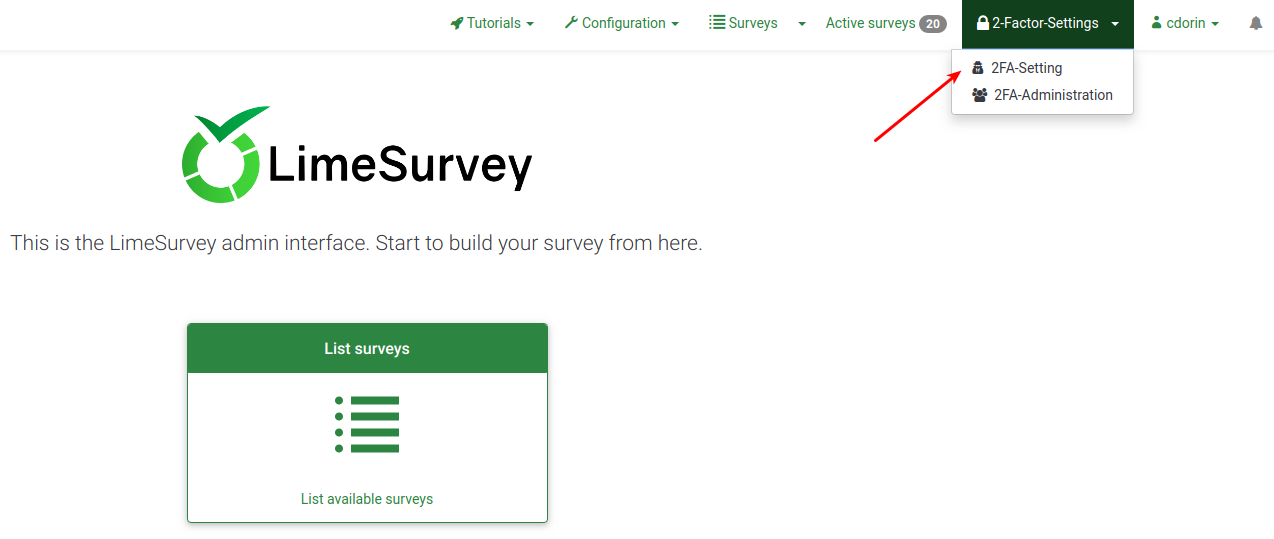
The dropdown menu includes the following two options:
- 2FA-Setting: Users can enable and manage their 2FA settings.
- 2FA-Administration: With the right permission, you can visualize whether the other instance users use 2FA or not.
2FA-Setting
If you haven't created any 2FA-token yet, the following page will be displayed:
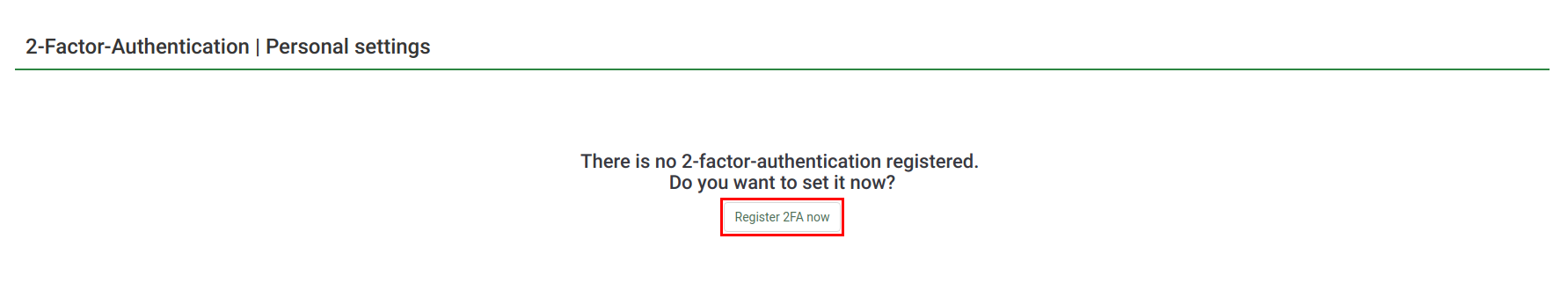
If you decide to create a 2FA-token, click on "Register 2FA now".
You will be prompted with a message box:
Select the 2FA authentication method.
- TOTP: Using Google Authenticator, Authy, ...
- Yubikey
When selecting a TOTP 2FA method:
- Scan the QR-code with your mobile phone. For a list of application recommendations, check this article.
- Enter the confirmation key displayed in your 2FA application.
When selecting Yubikey:
- Generate a code with your Yubikey in the confirmation key.
To confirm the creation of your 2FA-token, click on "Create 2FA binding".
Personal 2FA Settings
Once done, the following two options will be displayed in your personal 2FA settings:
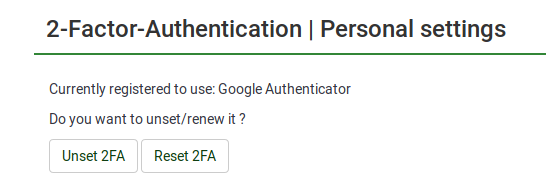
- Unset 2FA: Confirm your action to delete the 2FA-token associated to your account.
- Reset 2FA: If this option is selected, you will be asked to scan the new QR-code and introduce the new confirmation Key.
2FA-Administration
With the necessary permissions, you can have access to the 2FA user management panel from where you can check how many users activated 2FA.
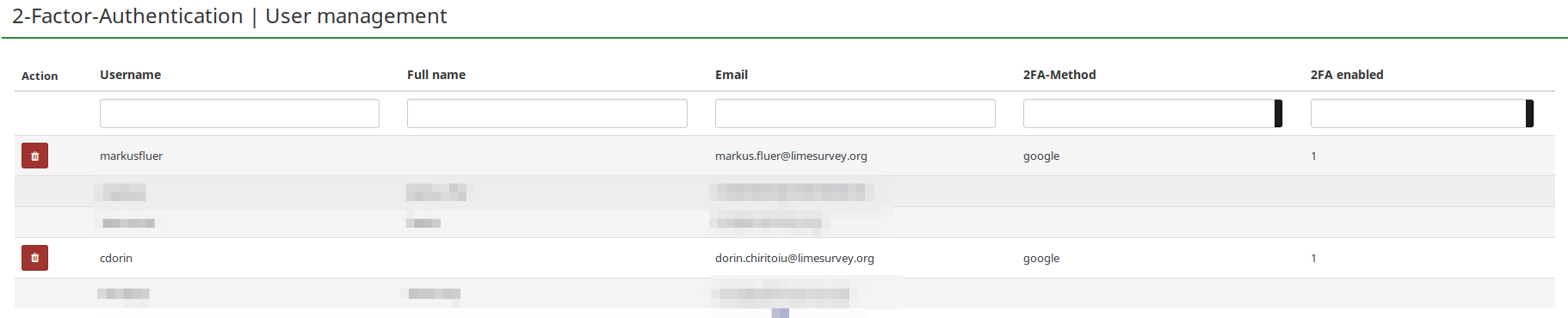
- Action: A red trash button is displayed in this column next to the users that have enabled 2FA. If someone asks to get the 2FA-token reset because he/she cannot log in anymore into your instance, you can delete the 2FA-token associated with his/her account from here.
- Username: All the instance users are listed under this column.
- Full name:The full name typed in here by your users is displayed in this field.
- Email: The email address corresponding to your users.
- 2FA-Method: The 2FA-method chosen by each user.
- 2FA enabled: If "1", it means that 2FA is enabled for the respective user.
FAQs
I am a super administrator and locked myself out. How can I delete my 2FA-token?
You will need access to your database and truncate the 2FA-related column.
How can I enforce 2FA to all my users?
Enable "Force 2FA" from the plugin configuration menu.
I use LimeSurvey Cloud. Do I have to purchase the plugin?
No. The plugin is already part of the core LimeSurvey plugins - you can enable it by accessing the plugin menu.